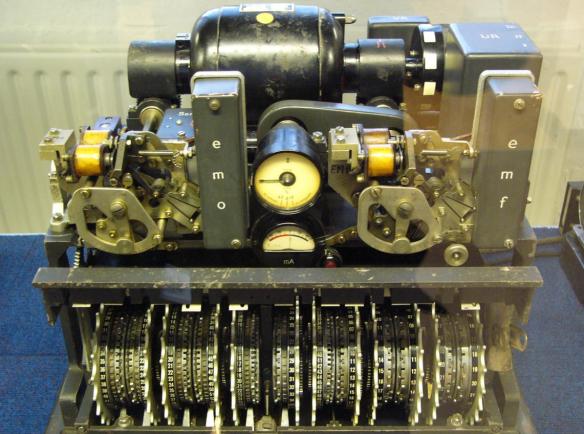
The Lorenz SZ42 machine with its covers removed.
The rotor principle was discovered independently by inventors in several countries, the most famous being German engineer Arthur Scherbius (1878–1929). Scherbius invented a three-rotor cipher machine, the Enigma, in 1918 (the last year of World War I). Scherbius tried unsuccessfully to sell his machine to commercial buyers, but he was ahead of his time; corporations did not begin to use encryption widely until the 1960s. Enigma was, however, purchased by the German government in 1926. At that time, Germany was busy rebuilding its military forces after its defeat in World War I and the humiliating terms of the Treaty of Versailles. Furthermore, the German military leadership had become aware that their pencil-and-paper field cipher, the famous ADFGVX cipher, had been broken by French cryptographers only a few months after its deployment in 1918, leading to at least one significant military defeat for the Germans. In order to prevent a repetition of the ADFGVX debacle, the Germans switched to Enigma as their primary system for secret communications.
The different branches of the German military also employed slightly different models of the Enigma cipher machine. In 1943, the German military deployed the SZ42 cipher machine for use over 26 crucial communications links. The SZ42 employed the stream-cipher technique, in which identical key-streams of pseudorandom characters are generated at both the sending and receiving end of the link and added, character by character, to the individual characters of the plaintext (for ciphering) or ciphertext (for deciphering). The German military did not replace Enigma with the SZ42 for general use because the SZ42’s complexity made it too heavy for the field.
The SZ42 cipher proved difficult for allied cryptographers to crack, as did another German cipher machine, the Geheimschreiber, first deployed by the German navy in 1942. However, Allied cryptographers cracked the Enigma, SZ42, and Geheimschreiber ciphers by building specialized devices to systematically try out possible keys for the decryption of messages. The first such devices— ”bombes,“ invented by Polish mathematician Marian Rejewski (1905–1980) and possibly named for the loud ticking noises they emitted while functioning—were electromechanical (i.e., used a combination of electrical currents and moving parts). Bombes sufficed for the Enigma cipher, but to crack the SZ42 and Geheimschreiber ciphers, the Allies built what is sometimes considered the world’s first electronic computer, the Colossus. The Colossus was based primarily on the ideas of British engineer T. H. Flowers (1905–1998) and British mathematician Alan Turing (1912–1954). (An ”electronic“ computer, as opposed to an electromechanical device, does not use moving parts to perform its calculations.)
Cipher-machine technology reached its peak in the Geheimschreiber and SZ42 cryptosystems, achieving a level of cryptographic security that could only be breached by the invention of a wholly new technology: the electronic computer. Nevertheless, all the major German ciphers of the World War II—and the primary Japanese cipher too, codenamed Purple—were broken by the Allies.
The Allies also used cipher machines during World War II, but with better luck, as the Axis governments did not succeed in breaking Allied ciphers routinely. The United States Army’s primary cipher machine descended from a compact device invented by Swedish inventor Boris Hagelin (1892–1983) in the mid-1920s. Hagelin’s cipher machine, originally designated the B-21, sold thousands of copies to the French military between 1934 and the French defeat in World War II. The U.S. Army purchased Hagelin’s machine after the German invasion of Norway in 1940 and redesignated it the M-209. More than 140,000 M-209s were manufactured before the end of the war. The M-209, like the SZ42, employed the stream-cipher technique, with matched generation of the key-stream at the transmitting and receiving ends of each link. Interestingly, this technique is still used today in applications such as digital pay- TV, file encryption, and communication with secure Web sites; however, electronic, rather than mechanical, generation of the pseudorandom key stream is used.